Have you ever wondered how your computer actually talks to the internet? How computers connect to the internet? Every time you open a website, send an email, or stream a video, your device is quietly working behind the scenes using basic networking protocols. These protocols are like rules of communication — ensuring that data moves securely, quickly, and to the right destination.
Without them, the internet would simply not work. In this networking tutorial for beginners, we’ll explore the most important networking protocols you should know as an IT beginner (looking for computer networking basics), student, or professional. These internet protocols explained the standards of communication between different devices on “how computers connect to internet.“
We’ll explain them in simple terms, share real-world use cases, and show how they impact cybersecurity, cloud computing, and online business today.
Table of Contents
Why Networking Protocols Matter
Think of the internet like a global postal system. Protocols are the standardized languages and methods that allow billions of devices — computers, routers, servers, and smartphones — to exchange information without confusion.
- For businesses, these protocols ensure secure transactions, email delivery, and reliable online services.
- For IT professionals, understanding protocols is critical for network troubleshooting, system design, and cybersecurity.
- For everyday users, they guarantee that when you type “google.com,” your browser knows where to go.
Now, let’s break down the most essential networking protocols that keep the digital world running smoothly.

List: Basic Networking Protocols with their Ports
- FTP (Port 21) helps transfer files between computers.
- SSH (Port 22) allows secure remote connections.
- TELNET (Port 23) is used for remote access but is less secure.
- SMTP (Port 25) sends emails.
- DNS (Port 53) translates domain names into IP addresses.
- HTTP (Port 80) loads web pages.
- POP3 (Port 110) receives emails.
- HTTPS (Port 443) is the secure version of HTTP.
- TCP ensures reliable data transmission.
- UDP allows faster but connectionless communication.
- ARP finds MAC addresses from IP addresses.
- RARP does the reverse by finding IP addresses from MAC addresses.
- MTP transfers media files.
- QOTD shows a “Quote of the Day.”
- PPP connects devices directly point-to-point.
1. FTP (File Transfer Protocol – Port 21)
What it does:
FTP is one of the oldest networking protocols, designed for transferring files between computers.
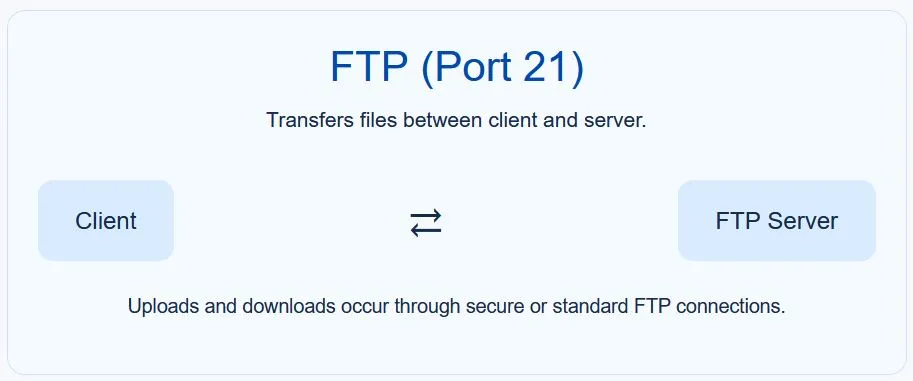
Use case:
- Uploading files to a website server.
- Downloading software or data from remote systems.
While FTP is still used, it has largely been replaced by secure alternatives like SFTP (Secure File Transfer Protocol), which encrypts the data.
Read also: What is Computer Networking? 10 Essential Facts for Beginners
2. SSH (Secure Shell – Port 22)
What it does:
SSH is a secure remote access protocol that allows you to log in to servers and devices over the internet.
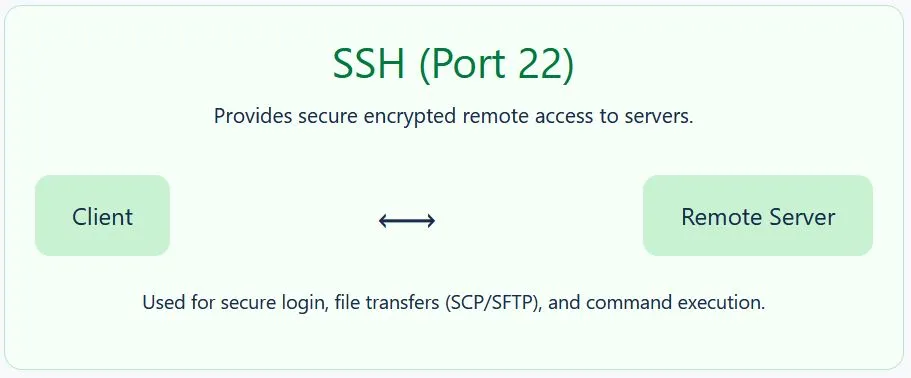
Use case:
- System administrators use SSH to configure servers.
- Cloud platforms like AWS or Azure rely heavily on SSH for secure management.

3. Telnet (Port 23)
What it does:
Telnet provides remote access to devices — but unlike SSH, it does not encrypt data.
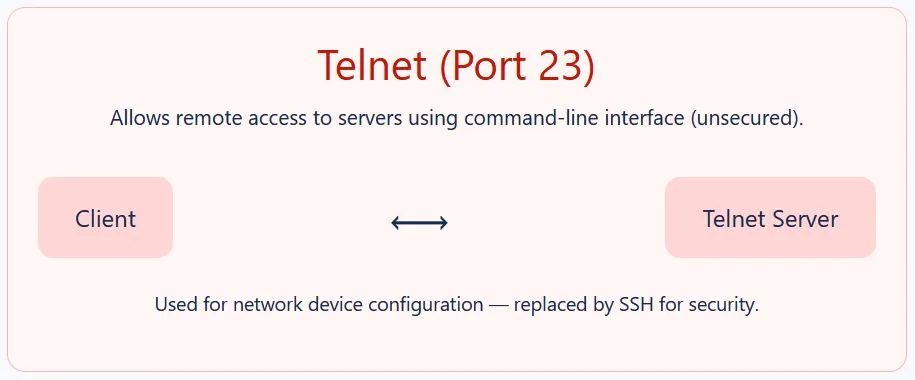
Use case:
- Rarely used today due to security risks.
- Sometimes still found in old networking equipment.
Security Tip: Avoid Telnet for critical systems — attackers can intercept credentials.
4. SMTP (Simple Mail Transfer Protocol – Port 25)
What it does:
SMTP handles sending emails between servers.
Use case:
- When you click “Send” in Gmail or Outlook, SMTP is working in the background.
- Businesses use SMTP servers for bulk email campaigns.
5. DNS (Domain Name System – Port 53)
What it does:
DNS is like the internet’s phone book. It translates domain names (like google.com) into IP addresses that computers understand.
Use case:
- Every time you open a website, DNS resolution happens.
- Businesses use DNS security services to block phishing and malware sites.
6. HTTP (Hypertext Transfer Protocol – Port 80)
What it does:
HTTP is the foundation of the web, allowing browsers to load web pages.
Use case:
- Every website runs on HTTP or HTTPS.
- Developers use HTTP for APIs and web apps.
But: HTTP is not secure — all data is visible in plain text.
7. POP3 (Post Office Protocol – Port 110)
What it does:
POP3 is an email protocol for receiving emails.
Use case:
- Downloads email from a server to your local device.
- Common in older email systems.
Today, IMAP is more popular because it syncs across multiple devices.
8. HTTPS (Hypertext Transfer Protocol Secure – Port 443)
What it does:
HTTPS is the secure version of HTTP. It encrypts communication between your browser and a website using SSL/TLS certificates.

Use case:
- Online shopping, banking, and logins.
- Required by Google for SEO ranking.
9. TCP (Transmission Control Protocol)
What it does:
TCP ensures reliable data delivery — like sending a package with delivery confirmation.
Use case:
- Websites, emails, and most internet apps rely on TCP.
- If a packet is lost, TCP resends it.
10. UDP (User Datagram Protocol)
What it does:
UDP is faster than TCP but connectionless. It doesn’t care if data is lost.
Use case:
- Online gaming.
- Video streaming.
- VoIP calls (Zoom, Skype).
Fun fact: UDP is why Netflix streams smoothly without waiting for every packet.
11. ARP (Address Resolution Protocol)
What it does:
ARP maps IP addresses to MAC addresses inside local networks.
Use case:
- Helps routers send data to the correct device.
- Used in troubleshooting network issues.
12. RARP (Reverse Address Resolution Protocol)
What it does:
RARP does the reverse of ARP — it finds the IP address of a device when only the MAC address is known.
Use case:
- Useful in older systems and diskless workstations.
13. MTP (Media Transfer Protocol)
What it does:
MTP enables media file transfers, especially between computers and smartphones.
Use case:
- Copying music/photos from your phone to PC.
- Used in digital cameras.
14. QOTD (Quote of the Day)
What it does:
QOTD is a fun protocol that delivers a daily quote from a server.
Use case:
- Rare today, but once used in learning environments.
15. PPP (Point-to-Point Protocol)
What it does:
PPP connects two devices directly over a serial link.
Use case:
- Used in dial-up internet connections.
- Still relevant in VPN tunneling and VPN protocol types.
The Bigger Picture: Why Protocols Matter for Cybersecurity and Business
Understanding networking protocols isn’t just academic — it has real-world value:
- Cybersecurity: Attackers often exploit weak protocols (e.g., Telnet, unencrypted HTTP).
- Cloud Computing: Businesses use secure protocols (HTTPS, SSH, DNSSEC) for cloud apps.
- Digital Marketing: Email protocols (SMTP, IMAP) ensure successful campaign delivery.
- VPNs and Remote Work: Protocols like PPP and SSL/TLS keep remote teams secure.
This makes networking protocols a high-demand skill for IT professionals — and a valuable knowledge area for businesses aiming to protect digital assets.
Final Thoughts
Networking protocols may sound technical, but they are simply the digital languages of the internet. From sending emails (SMTP) to browsing websites (HTTPS) or securing cloud servers (SSH), each plays a vital role in keeping the modern world connected.
If you’re starting in IT or just curious about how your devices talk to the web, learning these protocols gives you an edge. Whether you’re troubleshooting a home Wi-Fi issue, setting up a business email system, or diving into cybersecurity, you’ll find these protocols at the heart of every network.
FAQ on Networking Tutorial for Beginners
Q1. What are the most important networking protocols for beginners to learn?
The key ones are HTTP/HTTPS, DNS, SMTP, FTP, SSH, TCP, and UDP. These cover browsing, email, file transfer, and secure communication.
Q2. Why is HTTPS more important than HTTP today?
HTTPS encrypts your data, making it safe for online banking, shopping, and logins. Google also ranks HTTPS sites higher.
Q3. What protocol does online gaming use?
Most online games rely on UDP because it provides faster, low-latency communication, even if some data packets are lost.
Q4. How does DNS work in simple terms?
DNS translates human-friendly website names (like amazon.com) into IP addresses, so your browser can connect to the right server.
Q5. Is Telnet still used in 2025?
Rarely. It’s outdated and insecure. IT professionals now use SSH, which encrypts communication.
Q6. Which protocol is best for secure remote server management?
SSH (Secure Shell) is the industry standard for securely managing servers and cloud platforms.
Q7. What networking protocol is used for email delivery?
SMTP sends emails, while POP3 or IMAP receive emails. Businesses often combine them with spam filters and security layers.

Israr Ahmed is a technology educator and creator behind the YouTube channel “Israr Ahmed Technical,” where he shares practical IT, networking, cybersecurity, and software tutorials. He also runs DriveInTech.com and PakAider.pk to help learners and professionals grow in the digital world.