In a world where personal data is highly valuable, protecting your online privacy is no longer an option but a necessity. While many are aware of VPNs (Virtual Private Networks), few realize the potential of advanced configurations combined with powerful encryption techniques. This post will walk you through step-by-step guides, tools, and pro tips to fortify your privacy, incorporating cutting-edge technologies like OpenVPN, WireGuard, Tor, and IP masking. Ultimately, you will find the answer to the important question “How to Protect Your Privacy Online” with advanced VPN and Encryption techniques.
Section 1: What is VPN and Why is it Important for Online Privacy?
Understanding VPNs and Encryption Techniques
A VPN is a secure tunnel between your device and the internet. When you connect to a VPN server, your data gets encrypted, ensuring that hackers, ISPs (Internet Service Providers), and even government entities can’t easily track or monitor your activities.
Encryption works by converting your data into an unreadable format that only the intended recipient can decode. VPNs often use encryption methods like AES-256 to protect the data from interception.
Key Benefits of Using a VPN:
- IP Masking: Hides your real IP address, making it look like you’re browsing from another location.
- Data Encryption: Encrypts your internet traffic, preventing third-party access.
- Bypass Censorship: Helps access restricted websites in countries with heavy internet censorship.
Why You Should Go Beyond Basic VPNs
Basic VPNs provide some level of protection, but they can be vulnerable to advanced tracking techniques. For example, if your VPN leaks DNS (Domain Name System) data, your real IP address could be exposed. More advanced setups involve layering multiple encryption methods or using decentralized networks like Tor for anonymity.
Section 2: Advanced VPN Configurations for Privacy Enthusiasts
1. OpenVPN: Customizing for Maximum Security
OpenVPN is an open-source VPN protocol that offers the ability to customize encryption settings to meet the highest security standards. It’s known for its flexibility and is compatible with almost every major operating system.
Step-by-Step Configuration:
- Download OpenVPN from the official website and install it on your device.
- Choose Your Encryption Algorithm: Opt for AES-256 or ChaCha20. These are state-of-the-art encryption methods.
- Enable Perfect Forward Secrecy (PFS): This ensures that even if one encryption key is compromised, the rest of your sessions remain secure.
- Generate and Use TLS Keys: Transport Layer Security (TLS) keys help secure your VPN connection from attacks that try to intercept data during the handshake process.
Example VPN Configuration:
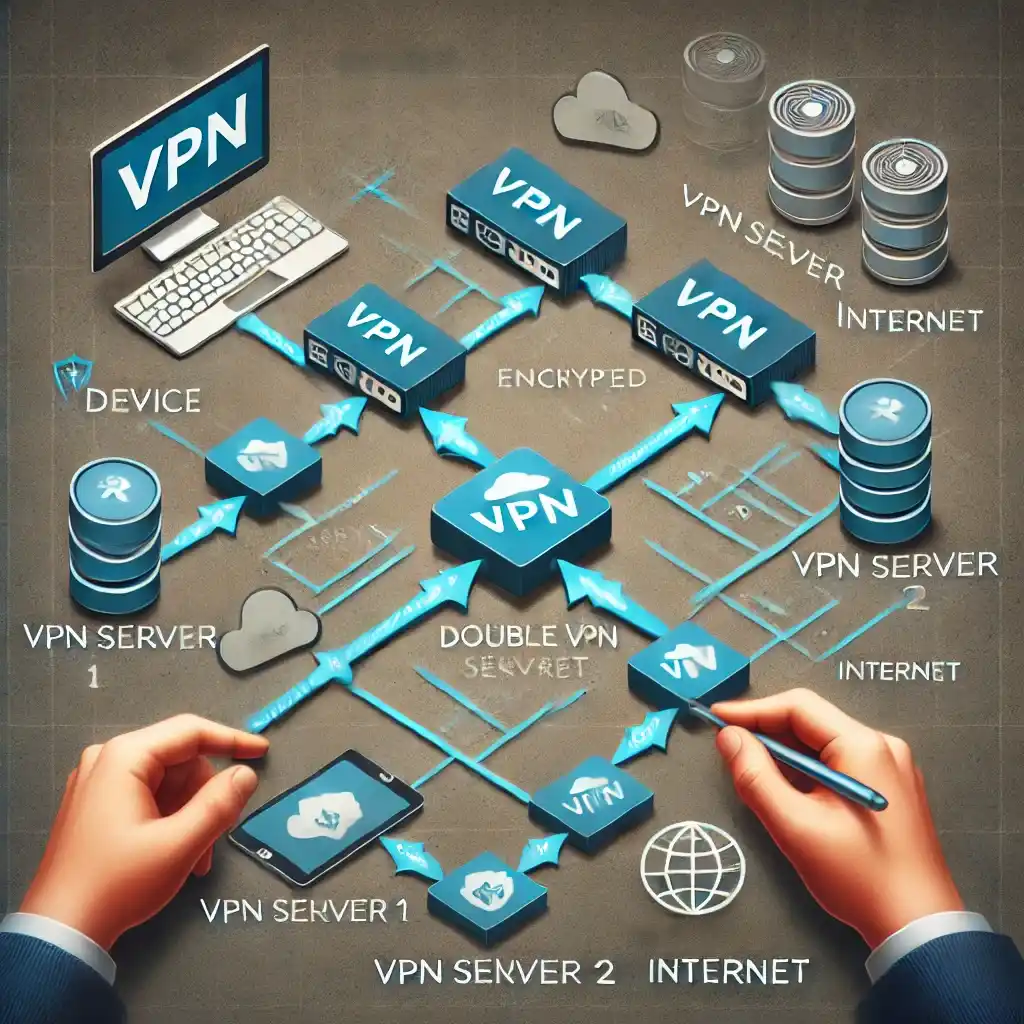
Here is the diagram illustrating the data flow through two VPN servers in a double VPN setup, showing how the user’s data gets encrypted and routed.
2. WireGuard: The Future of VPN Protocols
WireGuard is a newer VPN protocol that offers faster speeds without compromising security. It’s simpler than OpenVPN, making it a great choice for users who want a quick setup with modern encryption techniques.
Key Benefits of WireGuard:
- Speed: Faster than older protocols like IPSec and OpenVPN.
- Modern Cryptography: Utilizes ChaCha20 and Poly1305 for encryption.
- Simplicity: Fewer lines of code mean fewer vulnerabilities and quicker auditing.
Step-by-Step Configuration:
- Install WireGuard via a command line or GUI interface depending on your operating system.
- Generate Keys: You will need to generate public and private keys to establish a secure connection.
- Set up Peer-to-Peer Encryption: WireGuard operates in a peer-to-peer fashion, where both your device and the VPN server encrypt and decrypt traffic with the shared public key.
Example Visual:
- A diagram showing how WireGuard encrypts data and sends it through the tunnel from client to server and back.
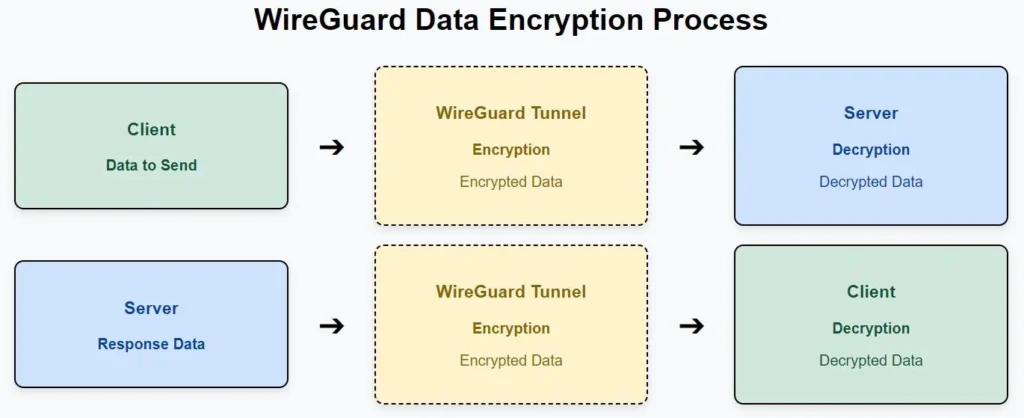
Explanation:
- Client Side:
- The Client has data that needs to be sent to the Server.
- This data is passed to the WireGuard Tunnel, where it is encrypted before transmission.
- Encryption:
- The WireGuard Tunnel encrypts the data using modern cryptographic techniques.
- Transmission:
- The encrypted data is sent through the tunnel over the internet to the Server.
- Server Side:
- Upon receiving the encrypted data, the Server decrypts it using the corresponding decryption process of WireGuard.
- The server processes the data and may send a response back to the client.
- Response:
- The response data is encrypted in the same way on the server side, sent back through the WireGuard Tunnel, and decrypted on the client side.
This process ensures a secure, encrypted connection between the client and server, protecting the data from eavesdropping or tampering during transit.
3. Double VPN: Multi-Hop for Extra Privacy
A Double VPN or Multi-hop VPN routes your traffic through multiple VPN servers. This method provides double encryption, making it significantly harder for anyone to track your activities.
Key Benefits of Double VPN:
- Double Encryption: Your traffic is encrypted twice, significantly improving security.
- Anonymity: Your traffic moves between two locations, adding more complexity for trackers.
How to Set It Up:
- Choose a VPN provider like NordVPN or Surfshark, which offers double VPN or multi-hop features.
- Enable the Double VPN option in the settings.
- Select the two locations where you want to route your traffic. The first server encrypts your traffic, and the second one re-encrypts it before sending it to its final destination.
Example Visual:
- A flowchart illustrating how data moves through two VPN servers before reaching the internet.
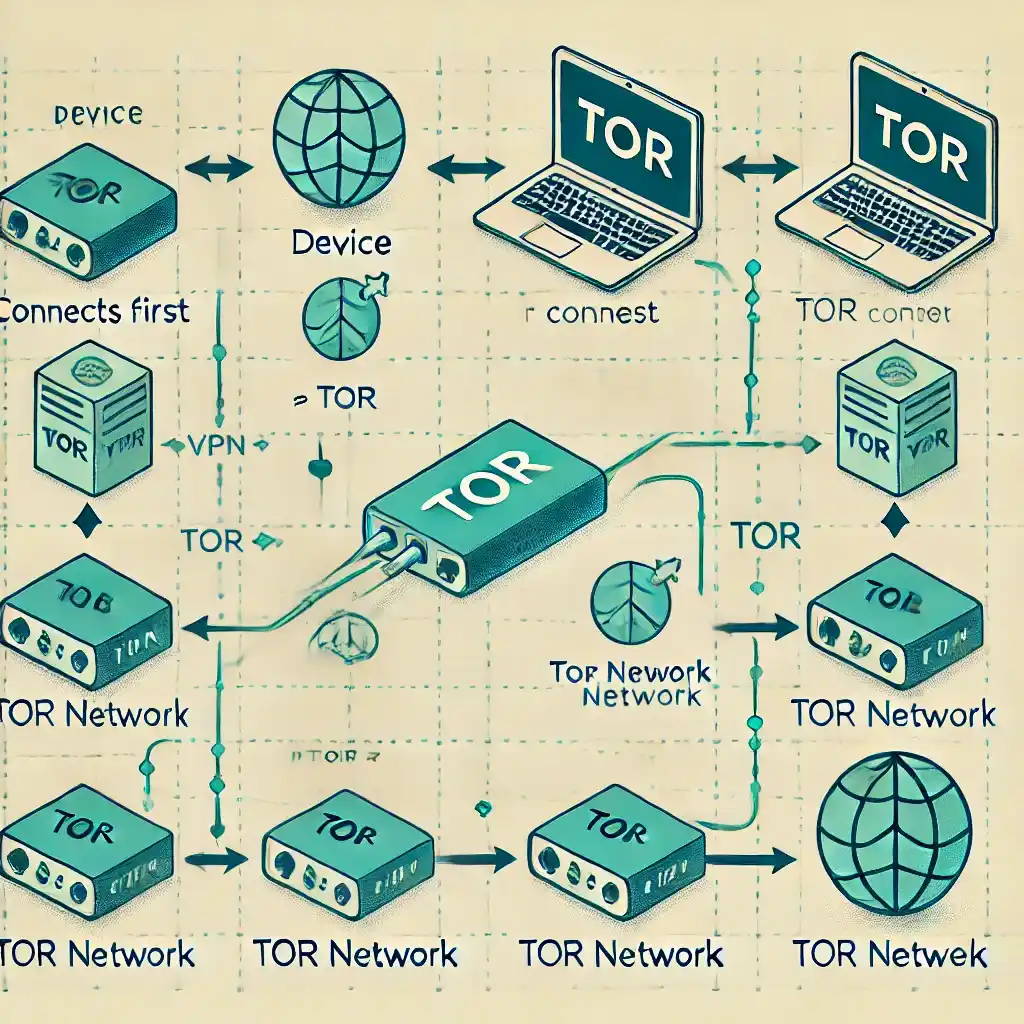
Here is the diagram illustrating the integration of Tor and a VPN, showing both the “VPN -> Tor” and “Tor -> VPN” setups.
Section 3: Combining VPNs with Tor for Ultimate Anonymity
Tor (The Onion Router) is a decentralized network that routes your internet traffic through multiple volunteer-operated servers. This creates layers (like an onion) that hide your original location and IP address.
Why Combine VPN with Tor?
- VPN + Tor: A VPN hides your IP address before your traffic enters the Tor network, providing an extra layer of security.
- Tor + VPN: In this setup, you first connect to Tor, then a VPN, which helps prevent your ISP from seeing that you’re using Tor.
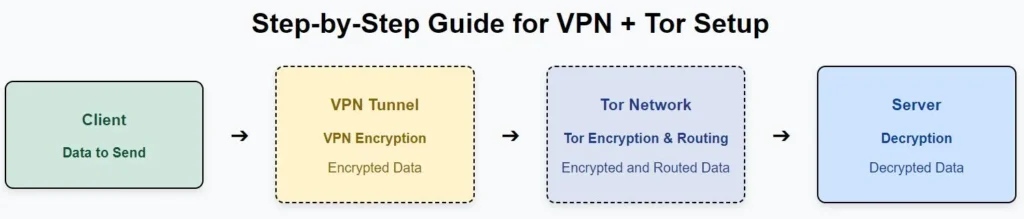
Step-by-Step Guide for VPN + Tor Setup:
- Activate Your VPN: First, connect to your VPN.
- Download Tor Browser: Install the Tor browser and launch it. Your VPN will shield your IP address, while Tor will anonymize your traffic.
- Test Your Setup: Use websites like check.torproject.org to ensure your traffic is routed through the Tor network.
Example Visual:
- A screenshot of the Tor Browser alongside a VPN connection status.
Section 4: Pro Tips and Best Practices
Tools to Strengthen Your Privacy:
- Tails OS: A privacy-focused operating system that leaves no trace of your activity. It can be run from a USB stick.
- DuckDuckGo: A privacy-centered search engine that doesn’t track your searches.
- ProtonMail: End-to-end encrypted email for secure communications.
- Pi-hole: Network-wide ad blocking that enhances privacy by preventing trackers.
Example Visual:
- Diagram showing how Tails OS, VPN, and Tor work together to create an untraceable environment.
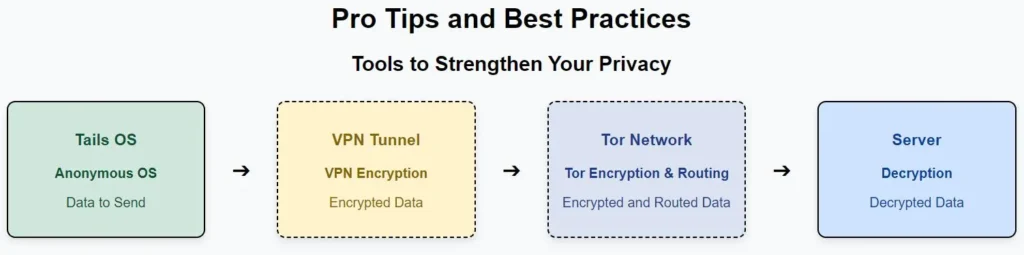
Pro Tips:
- Use a Dedicated VPN Router: Install your VPN directly on your router to secure all devices connected to your network.
- Turn on Kill Switches: A VPN kill switch ensures your internet connection is cut off if the VPN connection drops, preventing accidental exposure of your IP.
- Regularly Rotate VPN Servers: Switching VPN servers periodically ensures your browsing habits are harder to track.
Section 5: Bonus Tips and Extra Tools
Bonus Privacy Tools:
- Obfuscation Tools: Some VPN services (e.g., NordVPN) offer obfuscated servers that hide your VPN traffic, making it look like regular internet traffic and bypassing VPN restrictions.
- Split Tunneling: Allows you to choose which apps use the VPN and which don’t, offering flexibility and reduced bandwidth usage.
- DNSCrypt: Encrypts DNS traffic to prevent DNS leaks that can expose your browsing history.
Share a Downloadable Checklist:
To keep readers engaged, offer a downloadable PDF checklist with the key steps for setting up a secure and private online environment using advanced VPN configurations and encryption techniques.
FAQs on How to Protect Your Privacy Online with Advanced VPN and Encryption Techniques
Q: How is a double VPN more secure than a regular VPN?
A: A double VPN adds an extra layer of encryption by routing traffic through two servers, making it harder for anyone to track or decrypt your data.
Q: Is combining VPN with Tor overkill?
A: Combining the two provides maximum security for sensitive activities. It’s especially useful in countries with heavy surveillance.
Q: Can I use free VPNs for these advanced configurations?
A: Free VPNs typically don’t support advanced features like multi-hop or custom encryption. It’s best to invest in a reputable, paid service for optimal security.
Conclusion on Protect Online Privacy with VPN
Recap:
We’ve explored advanced VPN configurations, encryption techniques, and tools like Tor, which can greatly enhance your online privacy. Using OpenVPN or WireGuard with a double VPN setup or integrating Tor with your VPN can take your security to a new level.
Call-to-Action (CTA):
Share your experience with VPN setups or privacy tips in the comments below! And stay tuned for our upcoming posts on securing online communication and blocking trackers.






