What is UUID?
If you are looking the answer to the question “How to Get UUID”, then you are at the right post on our website driveintech.com
A UUID (UUID stands for Universally Unique Identifier) is a 128-bit identifier commonly used in software applications to uniquely identify objects, resources, or data. UUIDs are often represented as a string of hexadecimal characters, divided into five groups separated by hyphens (e.g., 550e8400-e29b-41d4-a716-446655440000). These identifiers are widely used in various applications where a unique reference is necessary, such as database records, file identifiers, or network resources.
UUIDs are valuable because they allow systems to ensure uniqueness without needing a central authority or continuous tracking of identifiers, making them ideal for distributed systems and decentralized data management.
Understanding UUID Structure
UUIDs follow a standardized structure specified by the ISO/IEC 9834-8. They are 128 bits long and typically divided into five groups of hexadecimal digits:
8-4-4-4-12- Example:
550e8400-e29b-41d4-a716-446655440000
Each section of a UUID serves a specific purpose, and various bits are assigned to distinguish UUID versions and variants.
3. UUID Versions and Their Use Cases
UUIDs have multiple versions, each with distinct methods for generation:
- Version 1 (Timestamp-based): Generated based on the timestamp and a unique machine identifier (usually the MAC address).
- Version 2 (DCE Security): Adds extra security by incorporating POSIX UID/GID data.
- Version 3 (MD5 Hash): Creates a UUID based on the MD5 hash of a namespace and name.
- Version 4 (Random): Randomly generated UUIDs, commonly used when uniqueness is essential but reproducibility isn’t.
- Version 5 (SHA-1 Hash): Similar to Version 3 but uses the SHA-1 hash.
Version 4 UUIDs are often the most popular due to their randomness and ease of use in distributed systems.
4. Benefits of Using UUIDs
UUIDs offer multiple benefits that make them a staple in modern software applications:
- Global Uniqueness: UUIDs are highly unlikely to collide, even across systems and databases.
- Decentralized Generation: UUIDs do not require a central authority to issue unique IDs.
- Compatibility: UUIDs work across many programming languages and database systems.
- Ease of Use in Distributed Systems: UUIDs are ideal for systems where resources are distributed across different servers.
5. Drawbacks of UUIDs
Despite their benefits, UUIDs have a few drawbacks:
- Size: UUIDs are large (128 bits), which can consume more storage and bandwidth compared to smaller identifiers.
- Non-sequential nature: UUIDs are not sequential, which can negatively impact indexing in databases.
- Readability: UUIDs are long and complex, making them difficult to read or manually process.
6. How to Get UUID in Different Programming Languages
Generating UUIDs is straightforward in most modern programming languages. Here’s a breakdown of how to get UUIDs in some of the most popular languages.
Python
In Python, the uuid module provides built-in methods to generate various UUID versions:
import uuid
# Generate a random UUID (Version 4)
unique_id = uuid.uuid4()
print(unique_id)
Java
Java’s java.util.UUID class allows for easy UUID generation:
import java.util.UUID;
public class GenerateUUID {
public static void main(String[] args) {
UUID uuid = UUID.randomUUID();
System.out.println(uuid.toString());
}
}
JavaScript
In JavaScript, you can use the crypto library in Node.js or a third-party library for the browser:
const { v4: uuidv4 } = require('uuid');
console.log(uuidv4());
<script src="https://cdnjs.cloudflare.com/ajax/libs/uuid/8.3.2/uuid.min.js"></script>
<script>
console.log(uuid.v4());
</script>
Or in the browser using UUID.js:
C#
C# provides the Guid class for generating UUIDs (known as GUIDs in .NET terminology):
using System;
public class GenerateUUID {
public static void Main() {
Guid uuid = Guid.NewGuid();
Console.WriteLine(uuid.ToString());
}
}
Ruby
Ruby’s SecureRandom library can generate UUIDs:
require 'securerandom'
unique_id = SecureRandom.uuid
puts unique_id
SQL
In SQL, some databases have built-in functions to generate UUIDs. Here’s how to get UUID in MySQL and PostgreSQL:
MySQL
SELECT UUID();
PostgreSQL
SELECT gen_random_uuid();
7. UUID Best Practices
When working with UUIDs, follow these best practices:
- Use UUIDs for Decentralized Applications: UUIDs are ideal for distributed systems where unique identification is essential across various locations or servers.
- Leverage UUID Version 4 for Randomness: Version 4 UUIDs provide high uniqueness, making them suitable for general-purpose use.
- Store UUIDs Efficiently in Databases: When storing UUIDs, consider using binary format to save storage space.
- Indexing Considerations: Due to their non-sequential nature, UUIDs can slow down indexing. You may want to consider other alternatives if indexing speed is a priority.
8. UUID Alternatives
Although UUIDs are widely used, there are some alternatives, especially if you prioritize smaller identifiers or require sequential order:
- ULID (Universally Unique Lexicographically Sortable Identifier): Like UUIDs but sortable.
- KSUID (K-Sortable Unique Identifier): A larger ID that is also sortable and includes a timestamp.
- NanoID: A customizable unique ID generator that’s shorter in length.
These alternatives may be more efficient for specific use cases where UUIDs may be too large or complex.
9. Common Uses of UUIDs in Applications
UUIDs are commonly used in various applications, including:
- Database Records: UUIDs help ensure unique records without relying on auto-increment IDs, beneficial for systems with distributed databases.
- API Resources: APIs often use UUIDs to uniquely identify resources in a way that avoids clashes.
- File Identification: UUIDs can be used to uniquely identify files in storage or within applications.
- Session Tracking: UUIDs can serve as unique session tokens for tracking user interactions.
10. Generating UUIDs in CLI (Command Line Interface)
UUIDs can also be generated directly from the command line using various tools. Here’s how to generate UUIDs on different operating systems:
Linux/Mac:
bash
uuidgen
Windows: On Windows, PowerShell you can generate UUIDs:
[guid]::NewGuid()
On Windows, you can get UUID by following the steps given below:
Step 1: Search the command line application “cmd.exe” as shown in the below image.
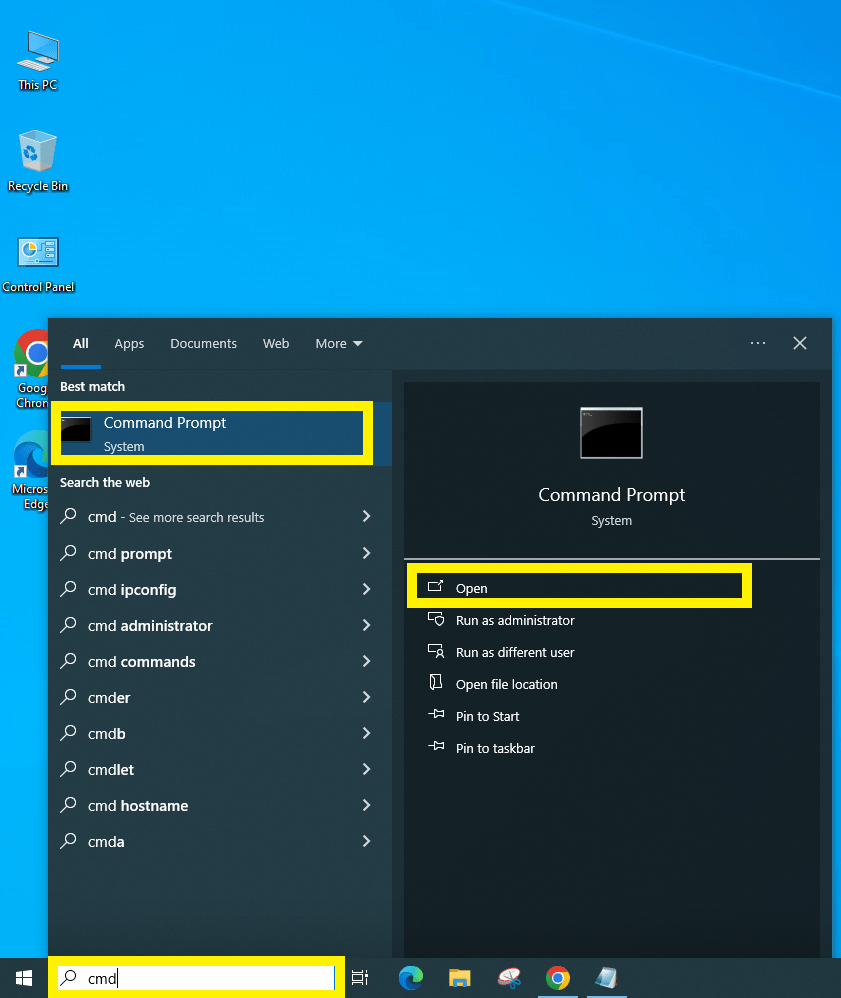
Step 2: You will see your username and “>” symbol; so you can type here the command given in the step 3.
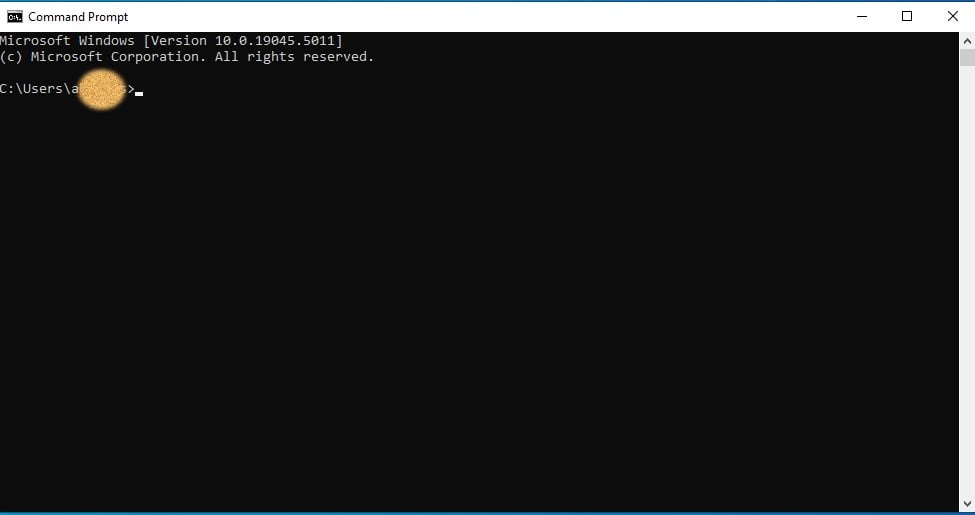
Step 3: Type the following command and press enter key from the keyboard. As show in the below snapshot.
wmic csproduct get uuid
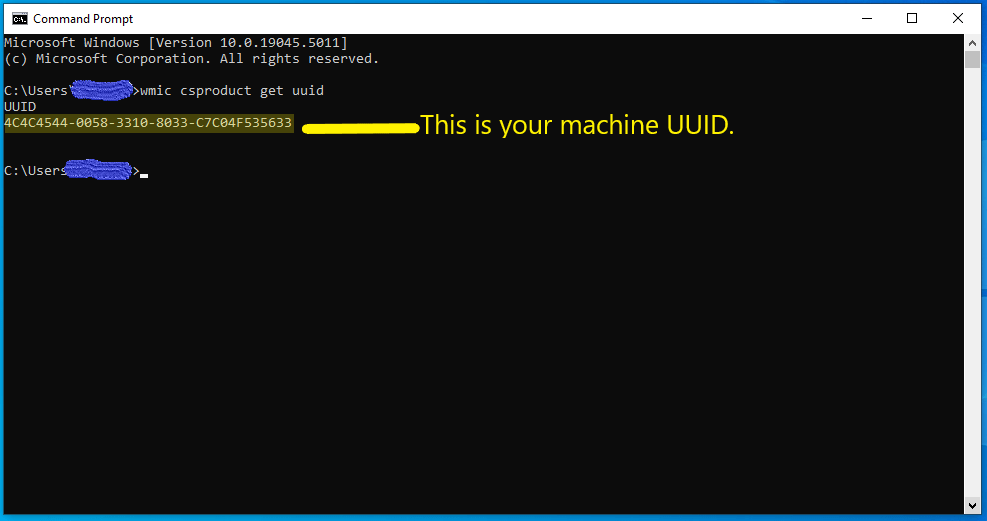
After the command, you can note the UUID for further usage and deploy your installation using SCCM that is Microsoft Configuration Manager solution product from Microsoft Intune.
11. Frequently Asked Questions
What is the difference between UUID and GUID?
UUID and GUID are essentially the same; UUID is the official ISO standard name, while GUID (Globally Unique Identifier) is Microsoft’s implementation.
Can UUIDs collide?
Though possible in theory, UUID collisions are extremely rare, especially with Version 4 UUIDs, as the odds of collision are astronomically low.
Are UUIDs secure?
UUIDs can be secure if used correctly. Version 4 UUIDs, generated randomly, are suitable for general use. However, cryptographic security measures should be considered for highly sensitive applications.
How are UUIDs stored in databases?
UUIDs can be stored as strings (commonly 36 characters in length) or as binary data. Binary storage is more efficient.
How do I convert UUIDs to binary?
Some programming languages, like Python and Java, have built-in methods to convert UUIDs to binary formats for efficient storage.
Can I use UUIDs as primary keys?
Yes, UUIDs are often used as primary keys, especially in distributed systems, though this may impact indexing performance.
12. Conclusion
UUIDs are invaluable for ensuring data uniqueness across decentralized applications, providing a flexible way to manage resources without needing a central authority. By understanding the structure, types, and generation methods of UUIDs, developers can leverage these identifiers to enhance data integrity, improve application scalability, and ensure a high degree of uniqueness across systems. Whether in databases, API management, or file handling, UUIDs serve as an essential tool for modern software applications.




“Outstanding post! The research quality and clarity blew me away. The way you’ve structured each point shows your deep understanding of the topic. I’ve learned so much from your expert insights.”
Thank you
“Simply extraordinary! ✨ Your in-depth analysis and crystal-clear explanations make this a must-read. The amount of valuable information you’ve packed in here is amazing.”
Thank you